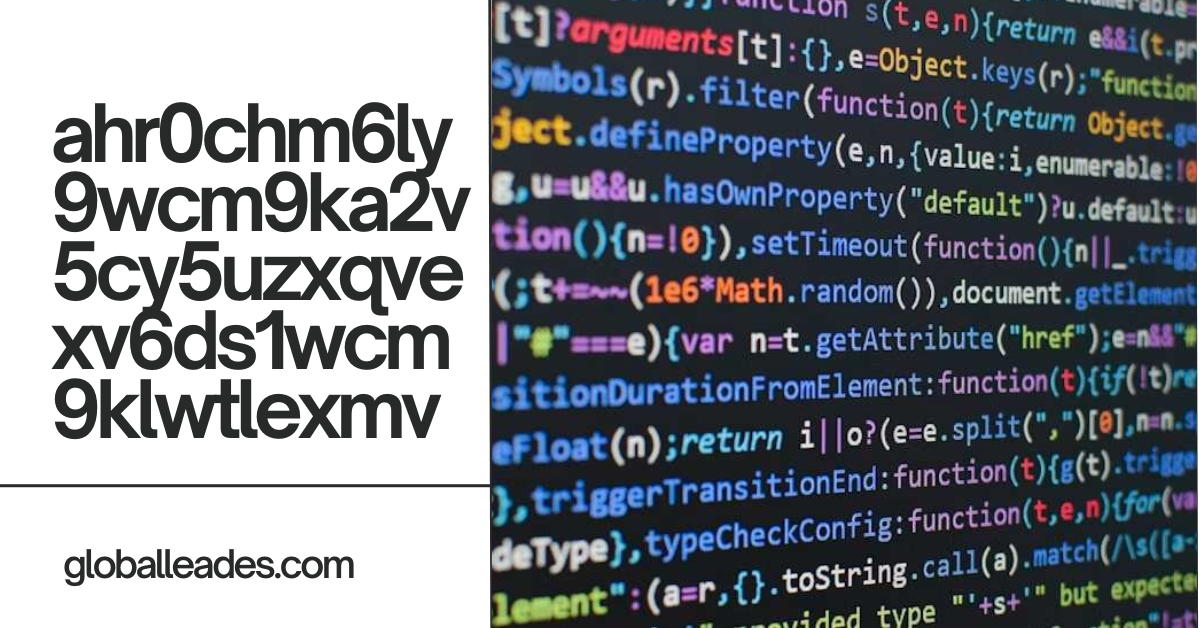
In the realm of cryptology, where secrecy and complexity reign supreme, there exist enigmatic codes that baffle even the most seasoned code-breakers.
One such code that has captured the imagination of many is “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv”. Its cryptic nature and mysterious origins have led to widespread speculation and intrigue among enthusiasts and experts alike.
As we embark on this journey to unravel its mysteries, we will delve deep into the intricate world of cryptography, exploring the history, significance, and potential implications of this enigmatic sequence of characters.
What is ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv?
“Ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” appears to be a string of characters encoded in Base64 format, a widely-used method for representing binary data in ASCII characters.
This encoding scheme allows binary data to be safely transmitted over text-based systems, such as email or the internet. Upon decoding, the true nature of the string is revealed, often as a URL or a piece of text containing encrypted information.
History of ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv
The exact origins of “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” remain shrouded in mystery. It could have emerged from the clandestine world of cryptography, where codes and ciphers are devised to conceal sensitive information from prying eyes.
Alternatively, it may be part of an elaborate puzzle or game designed for entertainment or educational purposes. Regardless of its origins, its presence on the internet has sparked widespread curiosity and speculation, with enthusiasts and experts alike seeking to unravel its secrets.
The Significance of “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv”
The significance of “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” lies in its enigmatic nature and the challenge it poses to code-breakers and puzzle enthusiasts.
Also Read: Käänjä – The Role Of Its In Communication In 2024
Its appearance in various online forums and platforms has sparked discussions and debates regarding its meaning and purpose. Some view it as a test of analytical skills and ingenuity, while others see it as an opportunity to explore the fascinating world of cryptography and encryption.
Deciphering the Code
Deciphering “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” requires a combination of analytical skills, pattern recognition, and intuition.
Code-breakers often employ various techniques such as frequency analysis, brute force methods, and the use of specialized software to unravel its secrets. Each approach presents its own challenges and requires a deep understanding of the underlying principles of cryptography.
Types of ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv
The types of “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” can vary, each presenting unique challenges and opportunities for analysis. Here are some common types:
- Encoded Messages: “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” may appear as encoded messages containing hidden information. These messages could be encrypted using various cryptographic algorithms, requiring decryption to reveal their true meaning.
- URLs: In some cases, “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” may serve as a URL leading to a webpage or online resource. These URLs could be links to encrypted content, websites, or platforms containing further clues or information.
- Data Encryption: Another type of “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” involves data encryption, where sensitive information is encoded to prevent unauthorized access. Deciphering such codes requires advanced cryptographic techniques and knowledge of encryption algorithms.
- Puzzle Solutions: Sometimes, “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” may be part of a puzzle or game, where solving the code leads to the next clue or stage. These puzzles can be designed for entertainment, educational purposes, or as part of a larger challenge or competition.
- Steganography: “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” may also be hidden within images, audio files, or other multimedia content using steganography techniques. Detecting and extracting such hidden codes requires specialized tools and knowledge of steganographic methods.
How does ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv Work?
The inner workings of “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” are governed by the principles of encoding and decoding.
By understanding the underlying algorithms and encoding formats, code-breakers can gain insights into its structure and unravel its hidden messages.
Also Read: Kääntäminen – Understanding the Basics of Translation In 2024
This requires a deep understanding of cryptographic principles, as well as proficiency in various programming languages and tools used for code analysis.
Unlocking the Potential applications
The potential applications of “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” are diverse and far-reaching, extending beyond mere curiosity and entertainment. Here are some potential applications:
Educational Tool: “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” can serve as a valuable educational tool for teaching cryptography, coding, and problem-solving skills. By engaging in the process of deciphering complex codes, students can develop critical thinking abilities and gain insights into the principles of encryption and decryption.
Security: “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” can be used to encode and transmit sensitive information securely. By employing encryption techniques, organizations can safeguard confidential data from unauthorized access and interception, ensuring the privacy and security of their communications.
Puzzle and Game Design: The enigmatic nature of “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” makes it ideal for puzzle and game design. Developers can incorporate encoded messages and cryptic clues into interactive experiences, challenging players to unravel mysteries and solve puzzles in immersive storytelling environments.
Communication: “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” can be used as a form of covert communication, allowing individuals to exchange sensitive information discreetly. By encoding messages using cryptographic techniques, users can communicate securely without fear of interception or eavesdropping.
Digital Forensics: In the field of digital forensics, “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” may be encountered as part of an investigation into cybercrime or illicit activities. Forensic analysts use specialized tools and techniques to analyze encrypted data and uncover evidence, aiding law enforcement agencies in their efforts to combat cyber threats and protect digital infrastructure.
Entertainment and Recreation: “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” can also be used for entertainment and recreation purposes. Enthusiasts may create cryptic puzzles, treasure hunts, or interactive experiences that challenge participants to decipher codes and unlock hidden secrets, providing hours of entertainment and intellectual stimulation.
Strategies of Code-Breakers
Code-breakers employ a variety of strategies and techniques to decipher “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv”.
Also Read: превоодач – Mastering the Art of Translation
These may include leveraging known patterns, exploiting weaknesses in encoding algorithms, or collaborating with other enthusiasts to pool resources and insights. Each strategy presents its own challenges and requires a combination of analytical skills, creativity, and perseverance.
Challenges of Perplexity
The inherent complexity and randomness of “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” pose significant challenges to code-breakers. Its unpredictable nature and potential for misdirection make unraveling its secrets a daunting task.
However, overcoming these challenges can be immensely rewarding, leading to new insights and discoveries in the field of cryptology.
Techniques of Code Analysis
Code analysis involves the systematic examination of “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” to identify patterns, anomalies, and potential clues.
By applying various analytical techniques, code-breakers can gain insights into its structure and uncover hidden messages. These techniques may include frequency analysis, statistical methods, and the use of specialized software tools designed for code analysis.
The Role of Intuition
Intuition plays a crucial role in deciphering “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv”. Sometimes, a hunch or gut feeling can lead code-breakers down unexpected paths and reveal solutions that defy logical analysis.
Also Read: Käämtäjä – Know The Importance In 2024
While analytical skills are essential, intuition can often provide valuable insights and shortcuts to solving complex codes.
Conclusion
In conclusion, “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” represents a captivating enigma that continues to captivate enthusiasts and experts alike. I
ts origins may remain shrouded in mystery, but its significance extends far beyond mere curiosity. This string of characters serves as a testament to the enduring allure of cryptography and the human quest for knowledge and understanding.
FAQs
Is “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” a secret government code?
There is no evidence to suggest that “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” is associated with any government agency or clandestine operation.
Can “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” be decoded using a simple online tool?
While some online tools may claim to decode it, the complexity of “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” suggests that specialized knowledge and techniques are likely required.
Does “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” have any connection to famous historical codes like the Enigma machine?
There is no known connection between “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” and historical cryptographic devices like the Enigma machine used during World War II.
Can “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” be a form of alien communication?
While speculation is intriguing, there is no evidence to suggest that “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” originates from extraterrestrial sources.
Is “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” a part of a viral marketing campaign?
There is no indication that “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” is associated with any marketing campaign or promotional activity.
Can “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” be cracked using traditional encryption methods?
While traditional encryption methods may offer insights, the unique nature of “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv” may require unconventional approaches for decryption.
Is there a prize or reward for successfully decoding “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv”?
As of now, there is no known prize or reward associated with deciphering “ahr0chm6ly9wcm9ka2v5cy5uzxqvexv6ds1wcm9klwtlexmv”. However, the satisfaction of solving the mystery may be its own reward.